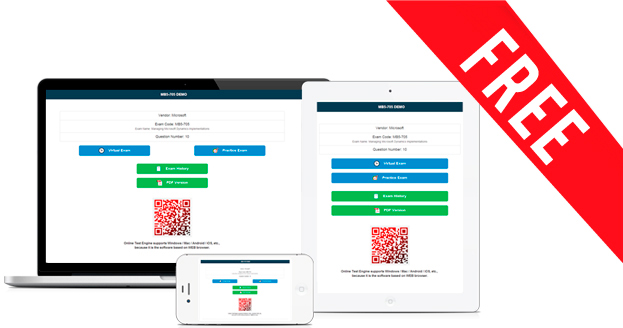
C2150-201 題庫產品免費試用
我們為你提供通过 IBM C2150-201 認證的有效題庫,來贏得你的信任。實際操作勝于言論,所以我們不只是說,還要做,為考生提供 IBM C2150-201 試題免費試用版。你將可以得到免費的 C2150-201 題庫DEMO,只需要點擊一下,而不用花一分錢。完整的 IBM C2150-201 題庫產品比試用DEMO擁有更多的功能,如果你對我們的試用版感到滿意,那么快去下載完整的 IBM C2150-201 題庫產品,它不會讓你失望。
雖然通過 IBM C2150-201 認證考試不是很容易,但是還是有很多通過的辦法。你可以選擇花大量的時間和精力來鞏固考試相關知識,但是 Sfyc-Ru 的資深專家在不斷的研究中,等到了成功通過 IBM C2150-201 認證考試的方案,他們的研究成果不但能順利通過C2150-201考試,還能節省了時間和金錢。所有的免費試用產品都是方便客戶很好體驗我們題庫的真實性,你會發現 IBM C2150-201 題庫資料是真實可靠的。
免費一年的 C2150-201 題庫更新
為你提供購買 IBM C2150-201 題庫產品一年免费更新,你可以获得你購買 C2150-201 題庫产品的更新,无需支付任何费用。如果我們的 IBM C2150-201 考古題有任何更新版本,都會立即推送給客戶,方便考生擁有最新、最有效的 C2150-201 題庫產品。
通過 IBM C2150-201 認證考試是不簡單的,選擇合適的考古題資料是你成功的第一步。因為好的題庫產品是你成功的保障,所以 IBM C2150-201 考古題就是好的保障。IBM C2150-201 考古題覆蓋了最新的考試指南,根據真實的 C2150-201 考試真題編訂,確保每位考生順利通過 IBM C2150-201 考試。
優秀的資料不是只靠說出來的,更要經受得住大家的考驗。我們題庫資料根據 IBM C2150-201 考試的變化動態更新,能夠時刻保持題庫最新、最全、最具權威性。如果在 C2150-201 考試過程中變題了,考生可以享受免費更新一年的 IBM C2150-201 考題服務,保障了考生的權利。

安全具有保證的 C2150-201 題庫資料
在談到 C2150-201 最新考古題,很難忽視的是可靠性。我們是一個為考生提供準確的考試材料的專業網站,擁有多年的培訓經驗,IBM C2150-201 題庫資料是個值得信賴的產品,我們的IT精英團隊不斷為廣大考生提供最新版的 IBM C2150-201 認證考試培訓資料,我們的工作人員作出了巨大努力,以確保考生在 C2150-201 考試中總是取得好成績,可以肯定的是,IBM C2150-201 學習指南是為你提供最實際的認證考試資料,值得信賴。
IBM C2150-201 培訓資料將是你成就輝煌的第一步,有了它,你一定會通過眾多人都覺得艱難無比的 IBM C2150-201 考試。獲得了 IBM Certified Solution Advisor 認證,你就可以在你人生中點亮你的心燈,開始你新的旅程,展翅翱翔,成就輝煌人生。
選擇使用 IBM C2150-201 考古題產品,離你的夢想更近了一步。我們為你提供的 IBM C2150-201 題庫資料不僅能幫你鞏固你的專業知識,而且還能保證讓你一次通過 C2150-201 考試。
購買後,立即下載 C2150-201 題庫 (Fundamentals of Applying IBM Security Systems Identity and Access Assurance): 成功付款後, 我們的體統將自動通過電子郵箱將您已購買的產品發送到您的郵箱。(如果在12小時內未收到,請聯繫我們,注意:不要忘記檢查您的垃圾郵件。)
最新的 IBM Certified Solution Advisor C2150-201 免費考試真題:
1. A bank conducted online surveys for its customers to discover how it can improve its services.
One of the most common complaints from the bank's customers was that they have to remember so many passwords when using the bank's partner services (like stock trading, credit card point systems, and retirement investment management). The argument generally was "the bank wantedme to join the partner and even though they introduced me to them. I had to register independently and then remember another username and password." The bank would like to setup proper controls to address this most common complaint from its customers.
Which function does the bank need to use to solve this issue?
A) Role Based Access Control
B) Federated single sign-on
C) Cross domain single sign-on
D) Strong password encryption techniques
2. A customer has a requirement which is currently unavailable in an out-of-the-box product.
Who would be able to assist in troubleshooting the customer when developing a custom solution?
A) IBM Support
B) IBM LAB Services
C) Raise an enhancement request with IBM
D) IBM Sales
3. When designing an organization's tree structure in IBM Security Identity Manager, why is it advisable to put users and services in different containers?
A) It is easier to troubleshoot.
B) It allows segregation of duties.
C) It improves the directory's performance.
D) It simplifies delegated administration.
4. What is an example of IBM's user-based licensing type?
A) Authorized user
B) Public user
C) Private user
D) Authenticated user
5. What is a prerequisite for installing an IBM Security Identity Manager fix pack?
A) Make sure that the WebSphere server that is running the Security Identity Managerapplication is running
B) Ensure that the SOAP request timeout value is set to 150 or less by using the com.ibm.SOAP.requestTimeout property
C) Stop the LDAP server that is used to contain the Security Identity Manager data
D) Install the WebSphere Update installer for the appropriate WebSphere version as per the readme file of the fixpack
問題與答案:
| 問題 #1 答案: B | 問題 #2 答案: B | 問題 #3 答案: A | 問題 #4 答案: A | 問題 #5 答案: D |



 1039位客戶反饋
1039位客戶反饋











118.163.76.* -
當我訂購了 C2150-201 考試資料,我還是有點擔心。但是,在我使用了你們的考古題之后,我改變了我的想法。因為它涵蓋了所有的關鍵知識點。最後,我通過了考試。